HeyMilo Achieves SOC 2 Type 1 Compliance: What It Is & Why It Matters for Your Business
SOC 2 compliance is a pivotal security requirement for firms handling client data. It guarantees that businesses uphold strict privacy, security, and data protection regulations, thereby encouraging trust with partners and customers. This blog introduces SOC 2, its fundamental principles, and why it's a cornerstone for modern companies.

SOC 2 compliance is a pivotal security requirement for firms handling client data. It guarantees that businesses uphold strict privacy, security, and data protection regulations, thereby encouraging trust with partners and customers. This blog introduces SOC 2, its fundamental principles, and why it's a cornerstone for modern companies.
HeyMilo AI Has Achieved SOC 2 Compliance
Trust isn’t given; it’s earned.
Protecting your data, along with your candidates' data, is a responsibility we take seriously.
That’s why we’re proud to share that HeyMilo AI has achieved SOC 2 Type 1 compliance! This means we’ve passed a strict set of security and privacy standards to ensure your data is safe with us–and we’re working towards more...
Thousands of interviews are being conducted on our platform every month, and we’re committed to maintaining the highest standards of security. We’ve partnered with Delve to complete our audit and ensure that every requirement was met accurately. And we’re already working toward SOC 2 Type II—a more in-depth assessment that tests how well our controls perform over time, not just how they’re designed.
Now, we’d like to take a moment to explain what SOC 2 compliance means, why it matters, and how it keeps your information protected.
What Is SOC2?
It’s considered one of the most important security certifications a software company can get. Otherwise known as System and Organization Controls 2, was created by the American Institute of Certified Public Accountants (AICPA) to keep organizations safe from unauthorized access and other security risks (e.g. data breaches).
When you use HeyMilo's video interview software and AI tools for recruiting every piece of information is digitally stored. Working with critical data like this needs additional protection — like SOC 2.
SOC 2 follows the Trust Services Criteria, set by the AICPA and covers 5 principles: security, availability, processing integrity, confidentiality, and privacy. They are intended to help organizations protect sensitive data, maintain reliable system performance, and uphold privacy standards across all operations/activities.
For secure companies, SOC 2 compliance is a must when selecting an online service provider.
Why Does It Matter?
Being SOC 2 Type 1 compliant means our team has implemented the right controls to protect your data. And Type II, which we’re now actively pursuing, will go a step further by validating that those controls hold up consistently over time.
When you’re managing large-scale AI interviews, reaching out to thousands of candidates, or simply need to know where your data is going—SOC 2 compliance gives you peace of mind.

Explore The Different Types Of SOC2 Compliance
SOC reports come in three different varieties: SOC 1, SOC 2, and SOC 3.
- SOC 1 is for financial controls (for companies dealing with financial reporting).
- Type I checks controls at one point in time.
- Type II checks controls over a period of time.
SOC 2 is for security, privacy, and data protection. It's key for tech companies or any business that handles sensitive data. It has 5 main areas: security, confidentiality, privacy, availability, and processing integrity. Type I evaluates how controls are designed at a specific point in time. Type II evaluates how effective those controls are over a period of time.
SOC 3 is similar to SOC 2 but it’s a public summary with less detail.
Understanding SOC 2 Compliance Requirements
SOC 2 identifies the criteria required to maintain strong information security, allowing each firm to establish policies and processes related to its particular goals and operations.
Below are the details of the five service criteria:
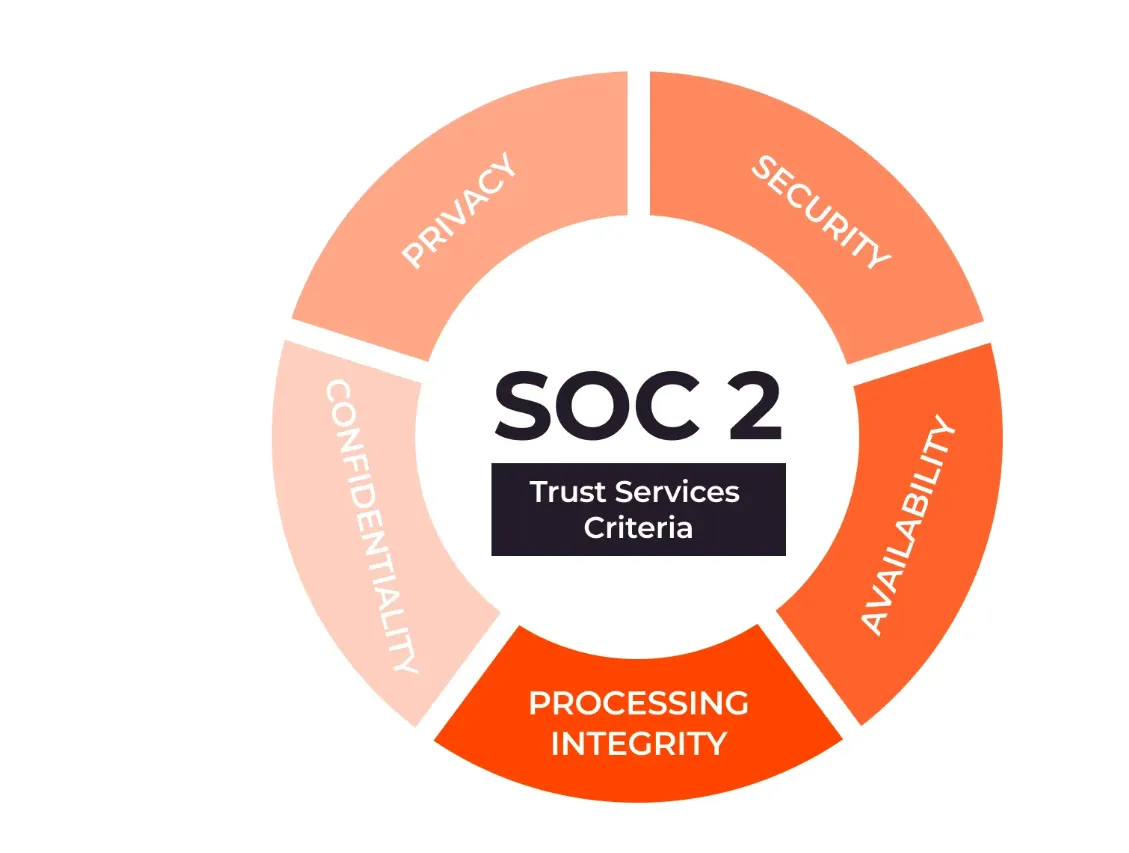
1. Security
Security is the defence against unwanted access/misuse of data and systems. To prevent this, IT security infrastructures, such as firewalls, two-factor authorization, and other controls, can be utilized.
2. Availability
Availability refers to whether the information, software, or infrastructure is kept up to date and has controls for monitoring, activity, and maintenance. The criteria further assess and remove possible external risks and determine whether your business maintains minimally acceptable network performance levels.
3. Process Integrity
Processing integrity ensures that systems work as intended and are free from mistakes, omissions, delays, and unintentional or accidental manipulation. It means that permitted, thorough, and accurate data processing procedures are carried out as intended.
4. Maintaining Confidentiality
Confidentiality addresses the ability of the business to protect information that ought to be limited to a particular group of individuals or organizations. This includes customer information that can only be used for company employees' secret company data, such as business plans. Furthermore, trademarks and any other data must be protected by laws, rules, contracts, or agreements.
5. Privacy For Individuals
The ability of an organisation to protect personally identifiable information from unwanted access is called privacy. Names, social security numbers, addresses, and other identifiers like race, ethnicity, or health information are often how this information is presented.
Businesses that adopt SOC 2 must comply with the five TSCs.
Your Security Is Our Priority: Our Commitment To Keeping Your Data Safe
We are continuously improving our security protocols to conform to the highest standards in the industry. Achieving SOC 2 Type 1 compliance is just one part of our broader commitment to keeping your data safe. We’ve also achieved full GDPR compliance, ensuring that every interaction on our platform—from candidate interviews to system integrations—meets the highest standards of data protection and privacy. Read how HeyMilo AI achieved full GDPR compliance and what it means for hiring with AI here.
Thousands of AI interviews happen on HeyMilo each month. Whether you're screening at scale or managing sensitive candidate information, you can trust that our platform is built with enterprise-grade compliance, secure infrastructure, and thoughtful design at every layer.
From encrypted transcripts to role-based access controls, we’ve designed HeyMilo to keep your team efficient and your data protected—every step of the way.
Want to learn more? Request to view HeyMilo’s Trust Center for full compliance documentation at hello@heymilo.ai.
Yes, when it comes to interviews, we utilize an active proctoring layer, an AI-classifier, and more to detect cheating. We provide a trust score that indicates the likelihood of cheating.
Candidates are appreciating the ability to go beyond their resume and interview in a more interactive/adaptive manner compared to one way video interview software. We also have an average candidate satisfaction score of 4.6/5 - which highlights HeyMilo's conversational AI.
Questions can be configured with an objective evaluation criteria - so candidates are evaluated the way your recruiting team currently evaluates candidates.We additionally run 3rd party bias audit checks so with HeyMilo, you're leveraging ethical AI.





.webp)
.png)


